Millions of IPs Cached on our
Servers
Billions of IPs on Live Databases Worldwide
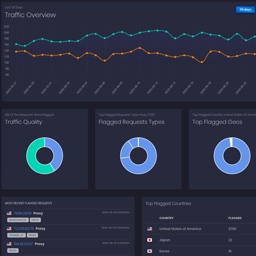
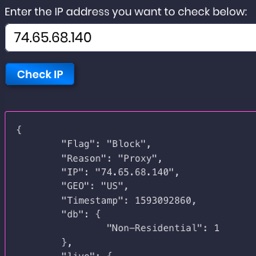
Detect Using our Fraud Scoring API
Click Fraud wastes an average of 20% in advertisers budget across all platforms.
Our automated service monitors your traffic and ads in real time, analysing each click, thus
leveraging data from billions of entries worldwide.
Watch Our 2 Minute Introduction Video
Create Your FraudSentinel Account
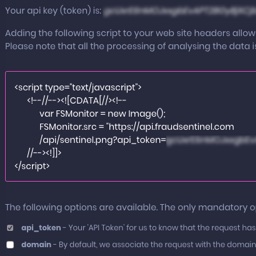
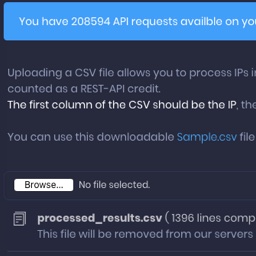
Add FraudSentinel FREE bots and fraud detection pixel to your web site and see the results in real time on our dashboard.
The main cause of Fraud in advertisement
|
Internet Bots An Internet bot, also known as a web robot, robot or simply bot, is a software application that runs automated tasks (scripts) over the Internet.[1] Typically, bots perform tasks that are both simple and structurally repetitive, at a much higher rate than would be possible for a human alone. The largest use of bots is in web spidering (web crawler), in which an automated script fetches, analyzes and files information from web servers at many times the speed of a human. More than half of all web traffic is made up of bots. Internet Bot - Wikipedia.com |
|
Click Farms A click farm is a form of click fraud, where a large group of low-paid workers are hired to click on paid advertising links for the click fraudster (click farm master or click farmer). The workers click the links, surf the target website for a period of time, and possibly sign up for newsletters prior to clicking another link. For many of these workers, clicking on enough ads per day may increase their revenue substantially and may also be an alternative to other types of work. It is extremely difficult for an automated filter to detect this simulated traffic as fake because the visitor behavior appears exactly the same as that of an actual legitimate visitor. Click farm - Wikipedia.com |
|
Malicious Publisher Malvertising (a portmanteau of "malicious advertising") is the use of online advertising to spread malware.[1] It typically involves injecting malicious or malware-laden advertisements into legitimate online advertising networks and webpages.[2] Online advertisements provide a solid platform for spreading malware because significant effort is put into them in order to attract users and sell or advertise the product.[3] Because advertising content can be inserted into high-profile and reputable websites, malvertising provides malefactors an opportunity to push their attacks to web users who might not otherwise see the ads, due to firewalls, more safety precautions, or the like. Malvertising - Wikipedia |
|
Scrapers Web scraping, web harvesting, or web data extraction is data scraping used for extracting data from websites. Web scraping software may access the World Wide Web directly using the Hypertext Transfer Protocol, or through a web browser. While web scraping can be done manually by a software user, the term typically refers to automated processes implemented using a bot or web crawler. It is a form of copying, in which specific data is gathered and copied from the web, typically into a central local database or spreadsheet, for later retrieval or analysis. Web Scraping - Wikipedia |
|
Brand Haters / Competitors Brand haters and competitors know the value of each click made on banners. In order to make sure your brand loses exposure, they will organize to make sure your campaign budget runs out before you can reach the real clients. |
|
Hackers Hackers hide themselves behind proxies or VPN's before doing an attack. Our solution can identify those hackers and expose the hacks before it occurs. |
We have sent you an email !
Click the confirmation link in that email to complete your registration.